
Business Continuity
Keep your business live and your critical data safe
Your data needs safe hands. No matter how well-planned your system is, there is always a risk of failure. That’s why we offer business continuity as a service. We manage back-ups and data recovery to protect your data at all times, so there’s no worrying about failover plans, storage, or monitoring your backup success ratio.
We keep everything running with on-time backups for all types of hosting. This gives you flexible access to the point-in-time recovery of your data. Our Business SLA offers 7-day on-site retention and our Enterprise SLA offers 30 days on-site retention plus 3 months off-site retention.
PointClick continuity processes
• Veeam Backup Agent that manages backups and effectively replicates your server
• Linux backups at Kernel level that ensure faster, more consistent restores
• Windows backups through a Windows driver that speeds backups and offers compatibility with Microsoft SQL Database
The PointClick Difference
• Our Enterprise SLA offers 30 days on-site retention and a weekly snapshot stored off-site for a rolling 3 month period
• We monitor backup success and health, rectifying issues immediately
• We guarantee to start data recovery from backup within 2 hours of request receipt

Managed Servers
Premium, flexible managed virtualization solutions
Enterprise-grade virtual servers managed in the cloud
Your company gains a valuable competitive edge if it’s more flexible and has a more responsive IT. With a Managed Cloud Server you get the benefits of cloud computing — flexibility, scalability, and cost-effectiveness — without the selection and administration of cloud components themselves.
We offer our customers first-class and highly flexible dedicated virtualization solutions based on the latest technology.
Through virtualization, we achieve high scalability, which is important for varying performance requirements or staging and development environments. In addition to full virtualization, we use Microsoft Hyper-V technology and Windows Azure Pack to provide a virtualized operating system container with Docker to give your company an agile service model.
Manged Cloud Servers inclusions
• 99.9% total infrastructure availability
• Industry-leading service-level agreements
• Scalable solutions as needed
• Technicians that monitor and provide regular operating system updates and patches
• Certified SysAdmin team with a breadth of cloud systems management knowledge

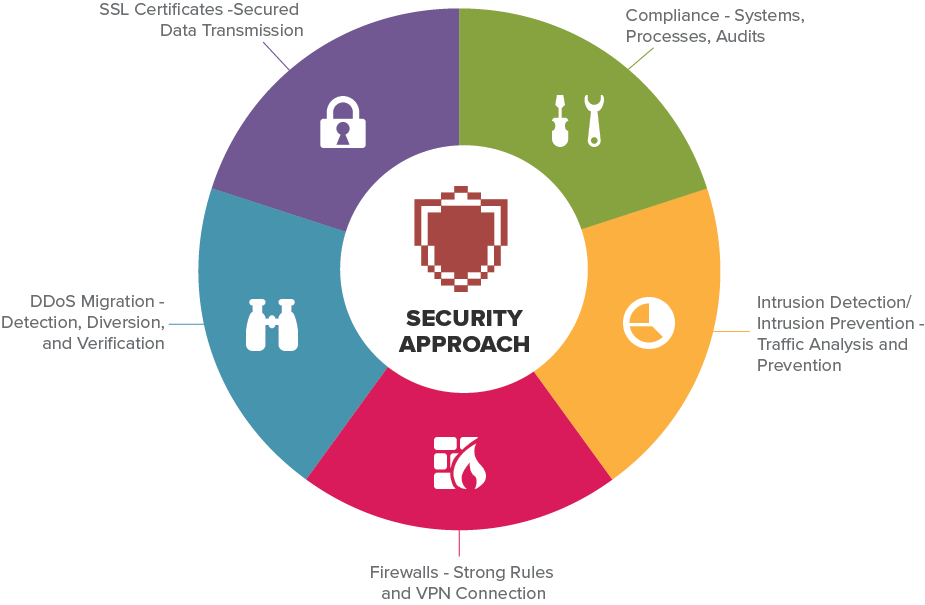
Manage Security
Rapidly achieve compliance and on-demand threat detection
A HIPAA-compliant data center is only one of the major components
With today’s dynamic economic climate, businesses spend much of their capital maintaining, monitoring, and managing their information systems and infrastructure. This comes from resources whose institutional knowledge and years of expertise could be better utilized providing value on internal projects designed to drive revenue.
With PointClick’s Managed Security Services, you can break free from wasting your talented resources on day-to-day task, and you can rest easy knowing that we’re keeping your business’ environment up and running and secure 24/7/365.
We also provide exceptional protection for Web Apps
- Certified ICSA WAF
- PCI 6.6 compliance featuring WAF and integrated scanner aid
- DoS protection for Network and Application layers
- User-behavior analysis
- Safeguards protecting against the OWASP Top 10
- Dynamic Protection that is always up-to-date
Related Articles

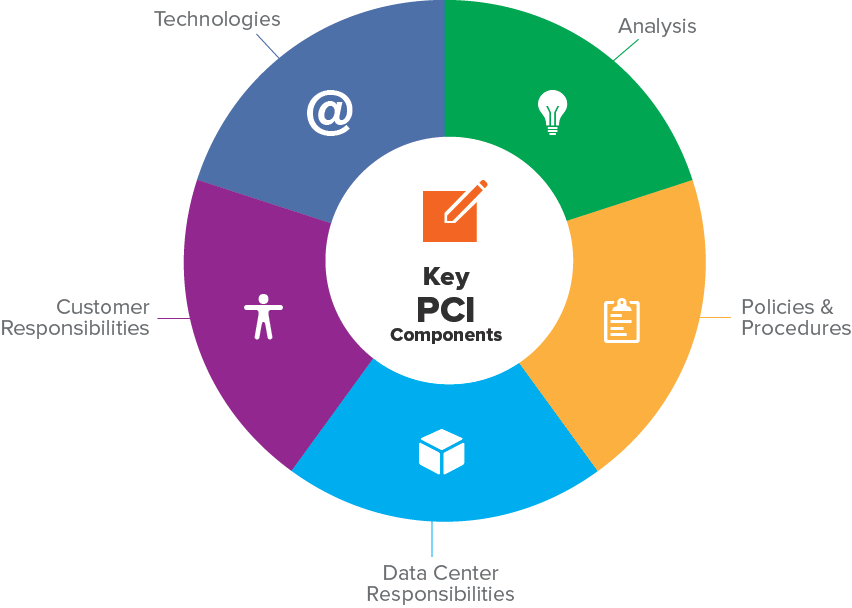
PCI Compliance
Reduce the cost and effort of becoming PCI–DSS compliant
Do you accept, store, or process credit or debit cards? If so, ensure that all credit/debit and transaction information is always protected and secure with Payment Card Industry Data Security Standard (PCI–DSS).
There’s no need to risk getting hit with fines or expulsion from major credit card programs. We can help you take the necessary steps to meet the requirements for protecting your customers’ sensitive personal data.
PointClick makes it easy. PCI-compliant web hosting requirements can be difficult to understand and implement, so we take that hassle off your hands, and you can stay focused on maintaining and growing a successful business.
It doesn’t end there — PointClick’s hosting provides your environment with the level of security required by all five major credit card companies. You also receive the routine network scans required by your Qualified Security Assessor (QSA) and off-server log management/audit trails — so, if you ever need to respond to forensic inquiries, you’ll be well-prepared.
We’re here for you 24 hours a day
Every single day — in the year. Just pick up the phone, and you’ll be talking to a real engineer within minutes. You can also email us and receive a response in 15 minutes or less.
Payment Card Industry Data Security Standard (PCI–DSS) — High-Level Overview
Do you know what’s going on behind-the-scenes of your network? PointClick’s 6-step path to PCI-DSS compliance covers every “little thing” that keeps your data safe and secure.
Build and Maintain a Secure Network
• Do not use vendor-supplied defaults for system passwords and other security parameters
Maintain a Vulnerability Management Program
• Develop and maintain secure systems and applications
Protect Cardholder Data
• Encrypt transmission of cardholder data across open public networks
Implement Strong Access Control Measures
• Conduct occasional portable device audits
• Search email archives for violations
• Investigate any breaches
• Manage security incidents
Regularly Monitor and Test Networks
• Make sure all security tools are up-to-date
• Inform all users of policies and procedures
• Investigate breaches
• Involve law enforcement
Maintain an Information Security Policy
• Block potential weak spots
• Manage security tools
• Terminate employees
• Prosecute offenders

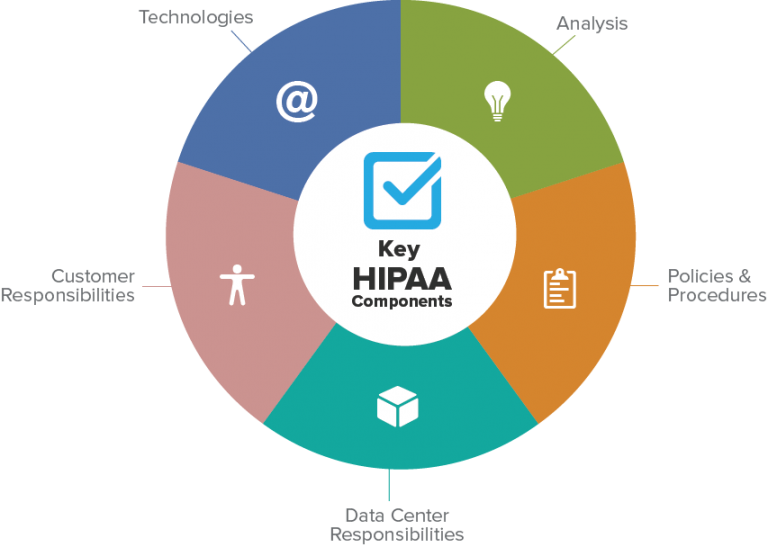
HIPAA Compliance
First-class fortified managed hosting solutions
PointClick understands that achieving HIPAA (Health Insurance Portability & Accountability Act – 1996) and PHI (Protected Health Information) Compliance can be time-consuming and costly to implement.
To simplify this process, PointClick offers a effective three-pillar approach that includes the system hardening, software & hardware configuration, and managed services you need to make achieving HIPAA and PHI compliance a reality.
Our Approach
This approach also includes Data Center and Customer Responsibilities. Both are crucial and often-overlooked components for achieving HIPAA Compliance.
Proven 6-Step Systematic Compliance Process
We developed this methodical 6-Step Compliance Process that guarantees your systems achieve HIPAA Compliance and we would love to walk through these steps with you at any time!
1: Review Status
• Modify your workflows for compliance
• Train your workforce
• Identify your subcontractors that handle data and implement Business Associates Agreements with them
2: Protect Yourself
• Make sure you understand the regulations
• Ensure that compliance important to yourself & your staff
• Make you fall in love with documentation of policies & procedures
• Ensure that your goals are enacted throughout your business
3: Prevent Data Breaches
• Conduct awareness programs
• Encrypt data
• Prevent data from being emailed or downloaded to portable devices
• Utilize security tools
4: Detect Data Breaches
• Conduct occasional portable device audits
• Search email archives for violations
• Investigate any breaches
• Manage security incidents
5: Contain Data Breaches
• Make sure all security tools are up-to-date
• Inform all users of policies and procedures
• Investigate breaches
• Involve law enforcement
6: Correct Data Breaches
• Block potential weak spots
• Manage security tools
• Terminate employees
• Prosecute offenders



